All businesses and different organizations deal with multiple files every single day, and that is even necessary also for the smooth functioning of the business. These files are being shared multiple times with a number of users. Credentials, let us talk about it first. Username, as well as passwords, are stored in the database of many organizations. When any user wants to log in, he or she enters the userId and password. The system compares the details entered by the user to the data stored in the database and checks if both are the same or not.
This method is weak and can be hacked by hackers easily. Thus, to overcome this problem, we have hashing algorithms.
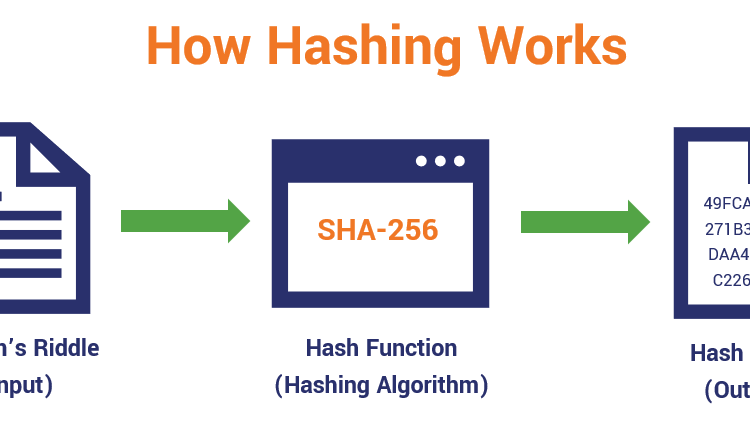
Hashing algorithms can be referred, to as slicing data into smaller and mixed-up chunks. It makes it extremely difficult for any end-user to get back to the real data. A hash function is a kind of algorithm in which normal text is converted into a different type of text, and that is hashed text. Therefore, it becomes tough for the hacker to decode it. Thus, it is a great step ahead in security measures. Let us discuss a few of the critical aspects which make a hash function ideal for use.
Key aspects for an ideal hash function:
● This function acts as a one-way function. It is not at all possible to get back to the original data, once the hash algorithm has been applied to it. Thus, if one gets a specific result, the ideal function will make sure that one doesn’t reach the initial data that was being used.
● The Avalanche effect is used effectively by the hash functions. There is a particular set of input that gives us the desired output, but if there is even a minor change in the input data, then it will become impossible to get the desired output. Even a very small change in the input will change the output drastically.
● The hash function should be effective as well as fast to compute. Getting output within seconds will never be a problem if the hash function is strongly built. One point to keep note is that the output of two different inputs should never be exactly similar to each other.
● It does not matter how many times one enters the input data; the output should always be the same data only. The output has to be the same irrespective of whenever one uses it.
In the above article, we have gone through the hashing algorithm in detail. In today’s world, where cyber theft, viruses and malware are increasing, it becomes necessary to have high security to protect the data. Hashing algorithms are one of the most effective methods of protecting important credentials and data. People and businesses need to understand the importance of data security in today’s world. Appsealing is one of the leading providers of security against various types of theft. People should take their assistance for securing their crucial data and applications.









![Is Tokyo Ghoul on Netflix? [How to Watch Online]](https://avctv.com/wp-content/uploads/2022/08/AAAABct1DaUzhEt4JeJFeDrmaE_4CGAu39fBN6poMx10hAlWlMRjkkAw84hjmuujWTy2wFC7_Pjnujec-_PqT1GCnnMFMJ15S04baJn1b0WvvbG6hrSNb31_GS4--120x86.jpg)





